恒安嘉新杯
简单的逆向分析
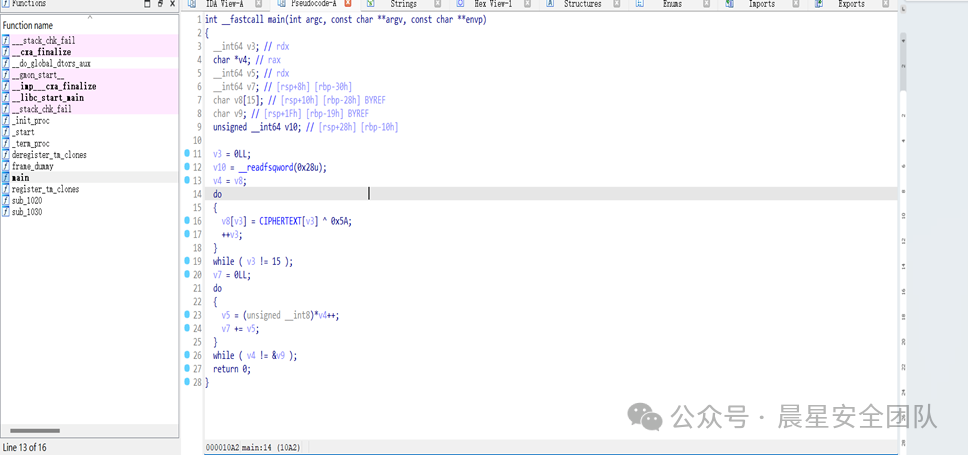
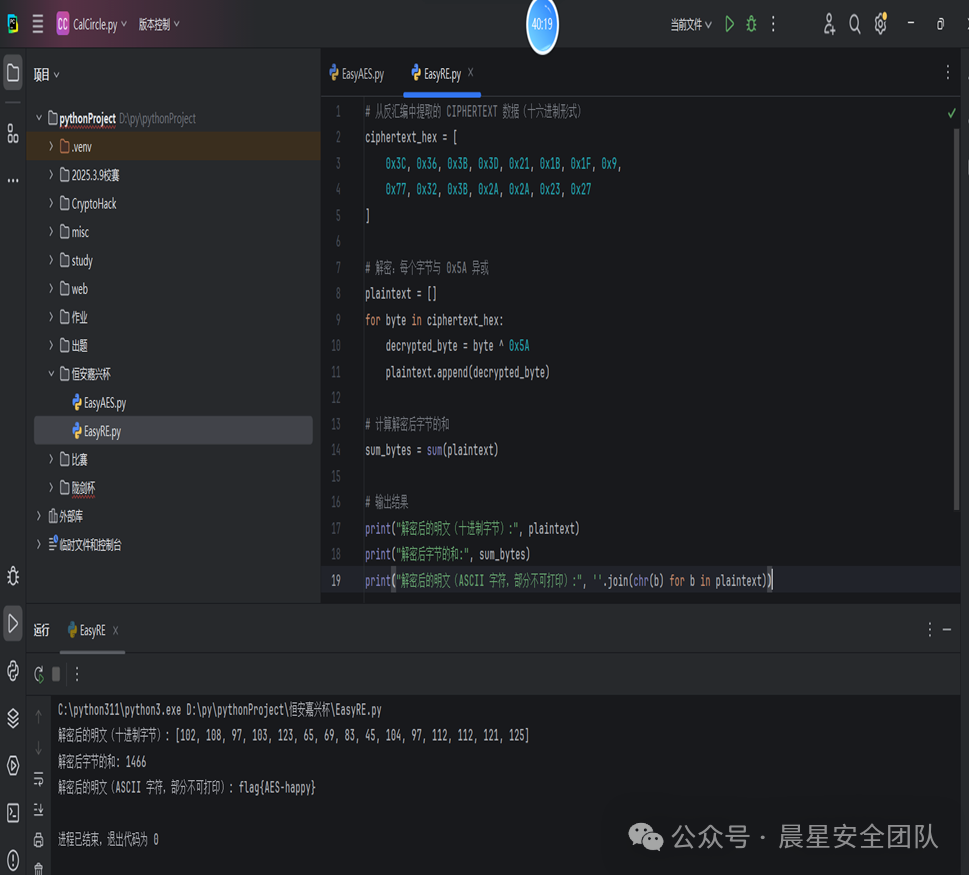
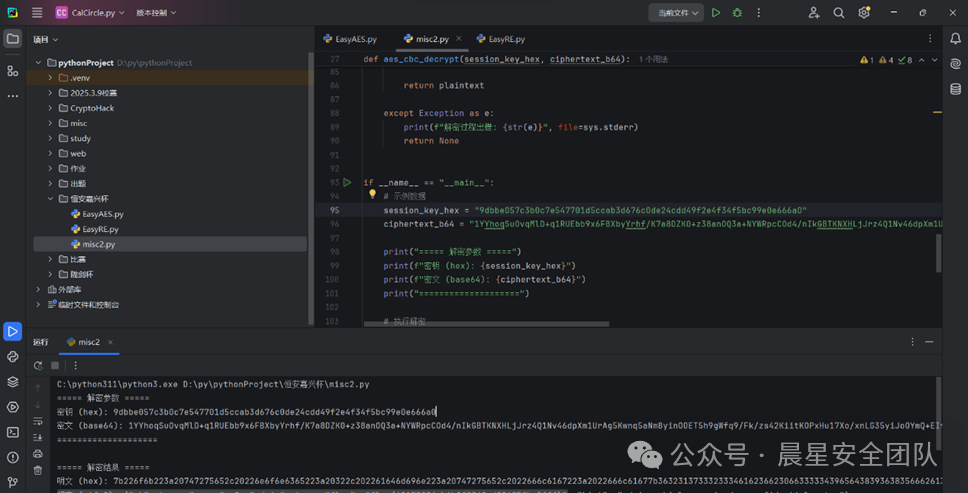
打开IDA找到main函数,发现CIPHERTEXT,直接双击密文
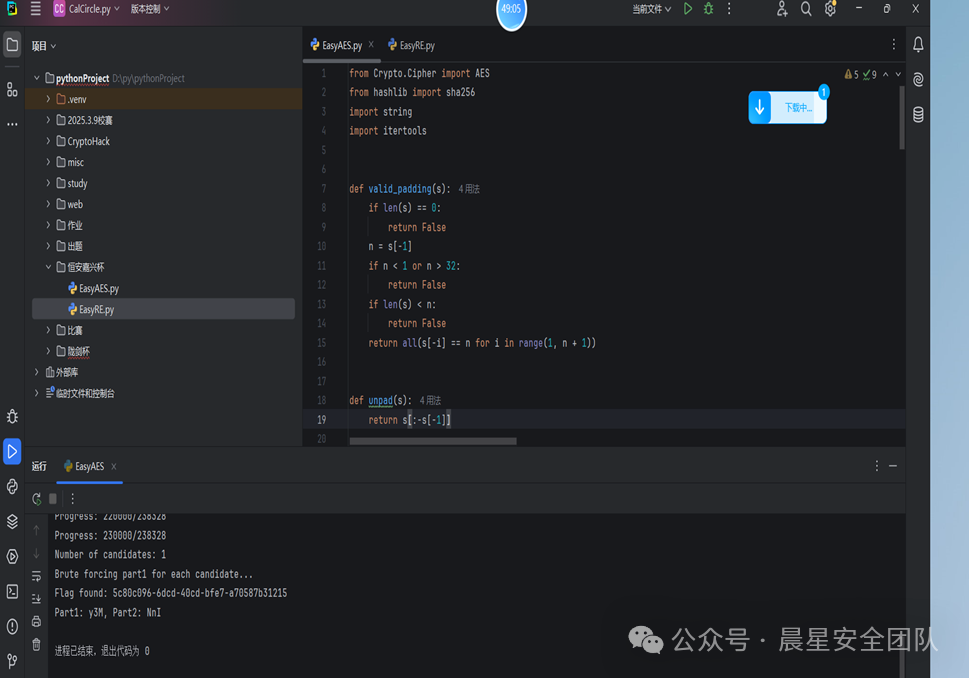
EasyAES
通过脚本可以得出答案
from Crypto.Cipher import AES
from hashlib import sha256
import string
import itertools
def valid_padding(s):
if len(s) == 0:
return False
n = s[-1]
if n < 1 or n > 32:
return False
if len(s) < n:
return False
return all(s[-i] == n for i in range(1, n + 1))
def unpad(s):
return s[:-s[-1]]
def decrypt_with_key(enc, key):
iv = enc[:16]
cipher = AES.new(key, AES.MODE_CBC, iv)
dec = cipher.decrypt(enc[16:])
return dec
def main():
c3_hex = "62343dfc3e978a1d580b54f345e1ed719c85ab15781acfe8ba3bcef1560c9cf54f187bc204c302a5ed4ebb5b5454151ba9b8b73841e17dc391c30a637ef8cfa14a25d01765231ef93a6faede2d66bad5d124201a2d278522bfd416de294677046d47f2827580cdcb9c0d3b18e4c0c68c8948aaefe4e684c7386b426db7898b5c2090047ff433bb6a75b38beaf81b7ad9404d2f09c642179697e9d3721eefc0eb12ba8c780a8d07672f70b00b9cadef74"
c3 = bytes.fromhex(c3_hex)
chars = string.ascii_letters + string.digits
candidates = []
print("Brute forcing part2...")
total = len(chars) ** 3
count = 0
for part2_tuple in itertools.product(chars, repeat=3):
count += 1
if count % 10000 == 0:
print(f"Progress: {count}/{total}")
part2 = ''.join(part2_tuple)
key1 = sha256(part2.encode()).digest()
try:
dec3 = decrypt_with_key(c3, key1)
except:
continue
if not valid_padding(dec3):
continue
c2 = unpad(dec3)
if len(c2) < 16:
continue
try:
dec2 = decrypt_with_key(c2, key1)
except:
continue
if not valid_padding(dec2):
continue
c1 = unpad(dec2)
if len(c1) < 16:
continue
try:
dec1 = decrypt_with_key(c1, key1)
except:
continue
if not valid_padding(dec1):
continue
c0 = unpad(dec1)
if len(c0) < 16:
continue
candidates.append((part2, c0))
print(f"Found candidate part2: {part2}")
print(f"Number of candidates: {len(candidates)}")
print("Brute forcing part1 for each candidate...")
for part2, c0 in candidates:
for part1_tuple in itertools.product(chars, repeat=3):
part1 = ''.join(part1_tuple)
key0 = sha256(part1.encode()).digest()
try:
dec0 = decrypt_with_key(c0, key0)
except:
continue
if not valid_padding(dec0):
continue
flag_padded = unpad(dec0)
try:
flag_str = flag_padded.decode('utf-8')
except:
continue
if len(flag_str) == 36 and flag_str.count('-') == 4:
if flag_str[8] == '-' and flag_str[13] == '-' and flag_str[18] == '-' and flag_str[23] == '-':
print(f"Flag found: {flag_str}")
print(f"Part1: {part1}, Part2: {part2}")
return
print("Done.")
if __name__ == '__main__':
main()失窃的工艺
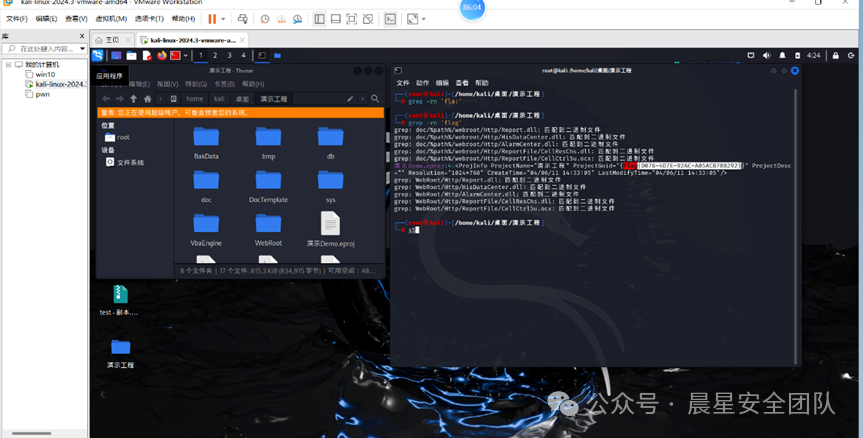
复制一份,发现可以变成ZIP格式解压,然后有一个有密码无法解压,但是另外一个演示工程能直接拖拽出来。
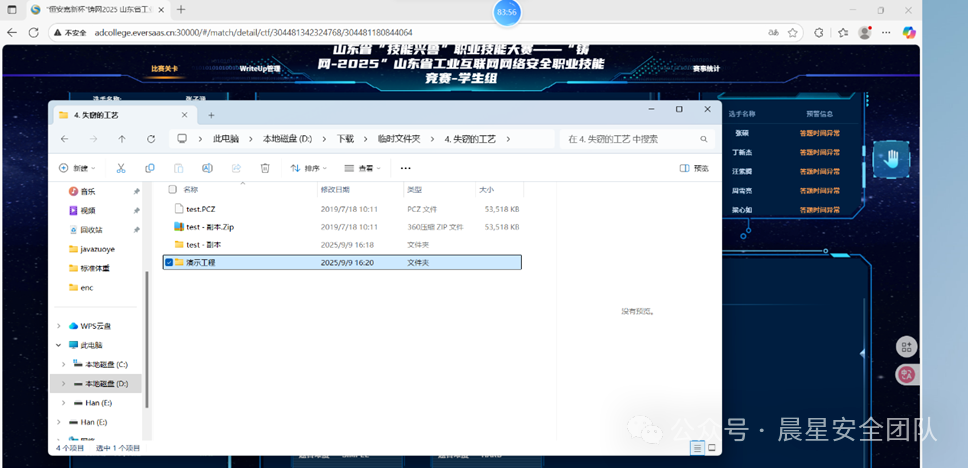
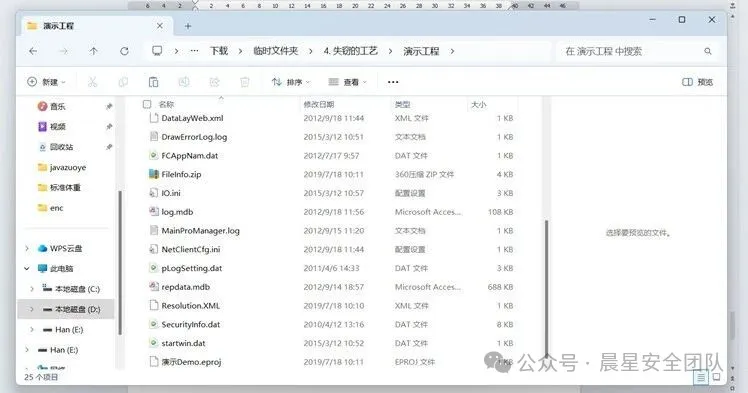
一个一个文件里面去找flag在Windows里面很麻烦,并且直接搜索也没有flag
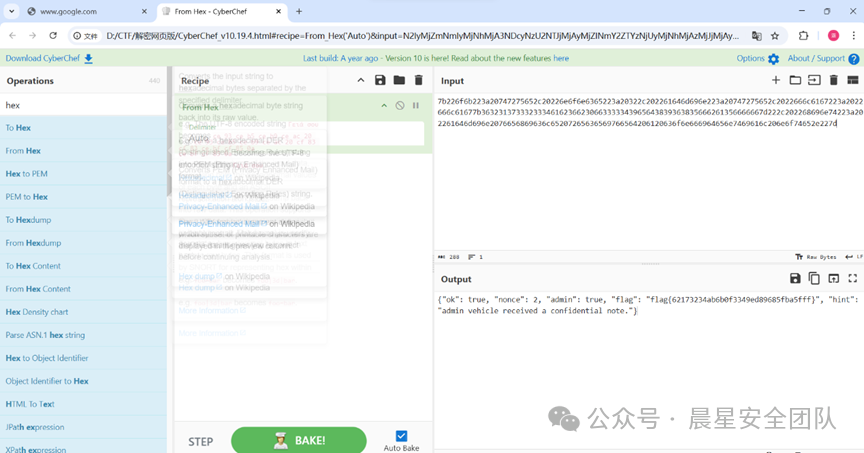
OTA流量分析
通过nata扫描发现,要去找TLS流量的密钥
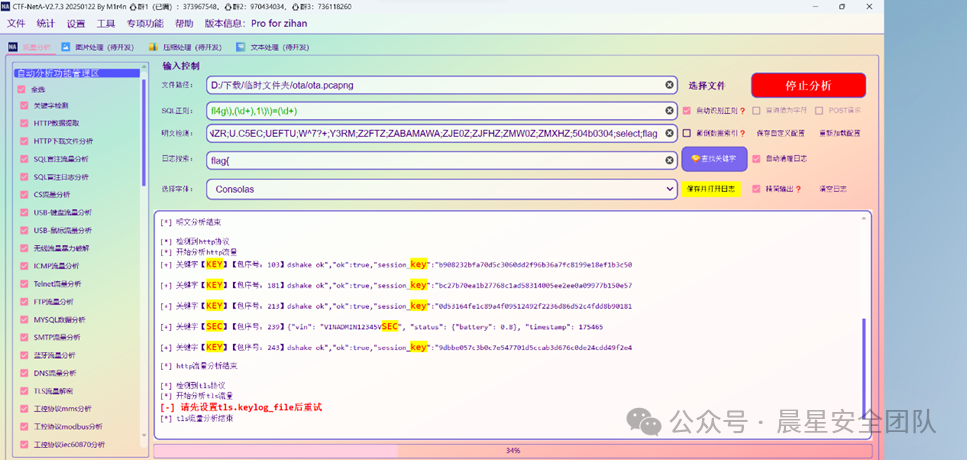
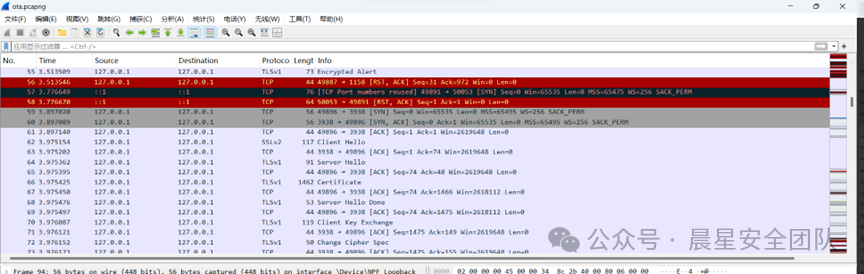
然后通过那个hello里面可以找到一个密钥和密文
{"message":"handshake ok","ok":true,"session_key":"b908232bfa70d5c3060dd2f96b36a7fc8199e18ef1b3c509efe4a86bf9339d90","vehicle_type":"normal"}
ALTaXk84WULvUwvHHoKpDlmW8PKnKIhyCZVl3kiI4Kca1NgiZDbUt6O6H1OAsZvUX7FyZsgjRJLolAEBnp0Lpg==
晨星安全团队----Zion_Cat